Strong and secure passwords: a practical guide to strengthening your online security
23. Oktober 2025

The importance of passwords
In the digital world, passwords are equivalent to the keys to our online life. They guarantee access to personal accounts (email, social networks, online banking) and professional systems (corporate accounts, business applications). However, they remain one of the most exploited weaknesses by cybercriminals.
“Passwords are like toothbrushes: they should be changed regularly, they are personal and should never be shared! Just as we take care of our hygiene every day, we must also take care of our cyber hygiene. Create unique and hard-to-guess passwords to protect your digital identity and personal information.”
(Source: Pplware)
In other words, creating unique and hard-to-guess passwords is essential to protect our digital identity and personal information.
What is a keyword?
A password is a sequence of characters or words that a user presents to a system as authentication information.
(Source: Associação para a Promoção e Desenvolvimento da Sociedade da Informação)
Recent statistics show the scale of the problem:
- - 3.8 billion credentials exposed in the first half of 2025 (UpGuard)
- - 88% of cracked passwords had fewer than 12 characters (Specops)
- - 81% of breaches involved weak or stolen passwords (Verizon DBIR)
- - 60% of employees reuse passwords, including security professionals
- - The average cost of a data breach is $4.5 million (IBM XForce, 2025)
Exemplos recentes:
- - 20/06/2025 - Portugal: more than 16 billion passwords exposed (Jornal de Negócios)
- - 23/05/2025 - Global: 184 million passwords lost (Apple, Facebook, Google, Microsoft) (Pplware)
These numbers indicate that most password-related security failures are largely avoidable through good practices.
The problem with weak and reused passwords
Despite the warnings, millions of users continue to use simple and predictable passwords. Examples like 123456, password, or birth dates remain among the most common worldwide.
This makes accounts extremely vulnerable to automated attacks that can test millions of combinations per second. And if the same password is reused across multiple services, a single breach can compromise an entire digital life.
Most common passwords in 2025:
123456/ 1234567889/ 12345678/ password/ qwerty123/ qwerty1/ 111111/ 12345/ secret/ 123123 ...
The word "password" is still used by around 700,000 people.
- - Other examples based on simple names:
dragon/ monkey/ football/ princess/ superman ...
(Source: Relatório NordPass, 2025)
These weak passwords are quickly exploited by hackers using high-performance software and, increasingly, Artificial Intelligence (AI).
How hackers exploit predictable passwords
Common passwords
Attackers automatically test the most popular combinations or default credentials in newly installed systems.
Brute force attacks
Programs such as Hashcat, John The Ripper, or THC Hydra test thousands of combinations per second.
Phishing
fraudulent messages trick users into providing their credentials, believing they are responding to legitimate entities.
Exposed personal information
Names, birthdays, or family members are easily found online.
Credential reuse
If one account is compromised, all accounts using the same password are also at risk.
Past data breaches
Attackers reuse old credentials exposed in previous leaks.
(Source: Escola da Internet)
And with next-generation hardware, the risk increases even further:
- - The GeForce RTX 5090 cracks passwords up to twice as fast as the 4090.
- - Studies show that 51% of passwords can be cracked in less than 1 minute using AI.
(Source: Tech Spot)
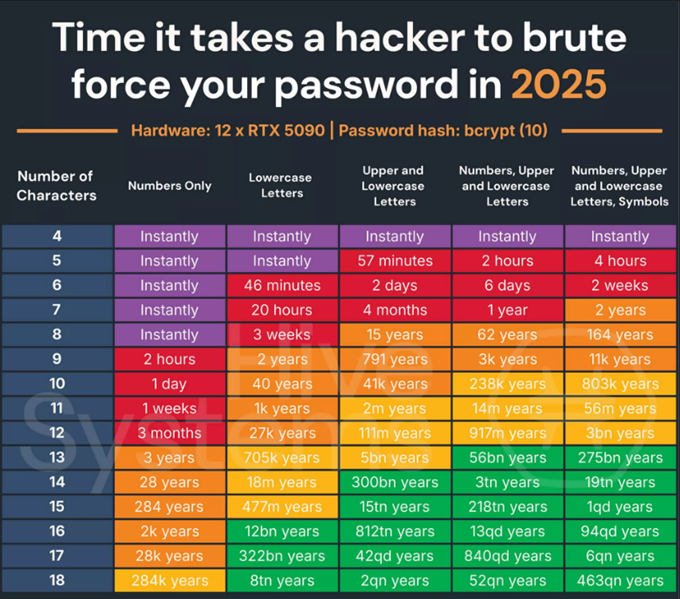
Time It Takes Using AI to Crack Your Password 2023
(Source: Pplware)
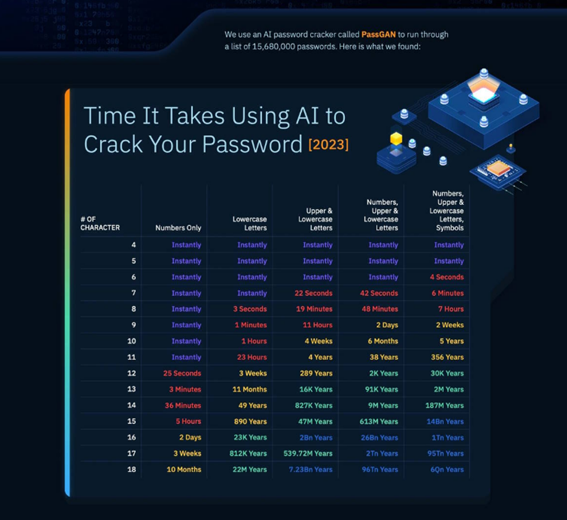
AI: 51% of passwords cracked in under 1 minute
Time Estimates to Crack Passwords with Quantum Computing
(Source: Hawcx)
Even when they seem harmless, these weaknesses have a serious impact on digital life. Some of the main consequences of compromised passwords include:
- - Identity theft
- - Access to bank or professional accounts
- - Data loss or blocking
- - Exposure of sensitive information
How to create a secure password?
The good news is that creating a strong password is not complicated. The secret is to make it long, varied, and unique.
- - At least 12 characters
- - Mix of uppercase, lowercase, numbers, and symbols
- - Avoid personal data or predictable patterns (e.g., birthdays, names, sequences)
Factors that contribute to choosing a secure password
Knowledge
- - Includes personal information easily discovered: name, date of birth, address, phone number, family members, friends, pets.
- - It should be avoided, as it makes the password easier to guess.
Simplicity
- - Use of default passwords (admin, 1234) or based on simple patterns (qwerty).
- - Predictable substitutions (e.g., P@55W0rd, S3cur1Ty) no longer offer security.
Structure
- - Long passwords, ideally passphrases.
- - Combination of letters, numbers, and special characters (~?!@#$%).
- - Do not include the username or personal data.
- - Avoid sequences (12345, qwerty) and repetitions.
Examples of easy-to-guess passwords
- - admin, password, administrator
- - Sequences (12345, abcdef)
- - Simple dates or common foreign words
Practical example of creating a strong password
- 1. Choose a name not of a close relative: João
- 2. Add a date or time: 1705
- 3. Add a theme or sport: Athletics
Applying structure rules:
- - JOa%17:05&Tismo
- - JoA%17.05&Atlet
Using the structure rules above, these passwords exponentially increase the time required to crack.
A 12-character password can take 30,000 years to be cracked by AI.
Common mistakes and best practices
Even the most careful users can make basic mistakes in password management. Many security breaches do not result from sophisticated attacks, but from avoidable oversights.
Essential rules
- - Use different passwords for each service (email, online banking, social networks, …)
- - Never share passwords with colleagues, friends, or family
- - Update regularly (ideally annually or whenever a compromise is suspected)
- - Avoid reusing the last 5 passwords in critical accounts
- - Do not store passwords in browsers, post-its, or text documents
- - Use a secure password manager
- - Change passwords when starting to use a new device
- - Enable multi-factor authentication (MFA) whenever possible
Most frequent password management mistakes
- - Reusing the same password across multiple services
- - Sharing credentials informally
- - Storing passwords in unencrypted files or emails
- - Underestimating “less important” accounts, which often serve as entry points
Quick checklist: Daily security best practices
- ✓ Always use strong and unique passwords
- ✓ Regularly update critical accounts (email, online banking, work)
- ✓ Never reuse passwords
- ✓ Enable MFA whenever available
- ✓ Use a reliable password manager
Multi-factor authentication (MFA)
Even a strong password may not be enough. Multi-Factor Authentication (MFA) adds an additional layer of protection, requiring two or more factors to confirm the user’s identity.
What is Multi-Factor Authentication (MFA)?
Authentication is the process that ensures that whoever is trying to access a system is really who they claim to be. MFA does not replace a strong password but complements it with an essential extra layer. It may involve:
- - Username and password
- - Digital certificates
- - Biometric factors (fingerprint, facial recognition, iris)
Types of authentication factors
- - Knowledge factors: something the user knows (password, PIN, security question)
- - Possession factors: something the user has (smartphone, physical token, access card)
- - Inheritance factors: something the user is (biometric data such as fingerprint or facial recognition)
- - Location factors: restricted by geolocation (e.g., blocking access from specific countries)
- - Behavioral factors: behavior patterns, such as gestures or typing style
Most common types of authentication
- - Password-based authentication
- - Certificate-based authentication
- - Biometric authentication
- - Token-based authentication
- - One-Time Password (OTP)
- - Single-Factor Authentication (SFA)
- - Two-Factor Authentication (2FA)
- - Multi-Factor Authentication (MFA)
- - Physical security keys
MFA in practice
MFA is one of the most effective ways to protect digital access. The most common example is 2FA (Two-Factor Authentication), which combines:
- - Username + password
- - A second factor, such as a code sent via SMS or through an authenticator app (Google Authenticator, Authy, Microsoft Authenticator)
In high-security environments, biometrics can also be combined with physical tokens (e.g., YubiKey).
The advantage of MFA is simple: even if your password is stolen, attackers will struggle to bypass the second barrier.
Services that already support MFA
- - Social networks (LinkedIn, WhatsApp)
- - Email (Gmail, Outlook, GoDaddy)
- - Financial and healthcare services
Best practice: activate 2FA/MFA on all accounts where it is available.
Password managers: Allies in security
With dozens of digital accounts, it is unrealistic to expect anyone to memorize all strong and unique passwords. Password managers emerge as an essential solution, functioning as secure digital vaults.
Main benefits
- - Automatic generation of strong passwords
- - Secure and encrypted storage
- - Autofill for websites and applications
- - Synchronization across devices
- - Alerts for weak or reused passwords
Note: always choose a reliable manager and never share your master password.
How password managers work
- - The user creates an account in the password manager and sets a master password.
- - The application stores, encrypts, and organizes all credentials.
- - With a single click, it fills login fields on websites and apps.
- - It can also generate strong and unique passwords whenever necessary.
Additional Features
Many managers also offer:
- - Secure form filling
- - Detection of phishing websites
- - Encrypted file sharing
- - Password strength reports
- - Multi-device synchronization
Popular examples
- - LastPass: simple interface, multiplatform, but limited free version.
- - 1Password: intuitive use and shared vaults; no free version and not open-source.
- - KeePass: free, highly customizable, but requires more technical knowledge.
- - Keeper: strong security, but expensive and harder for beginners.
- - Bitwarden: open-source, easy to use, with a completely free plan.
- - NordPass: offers password audits and 2FA; subscription is more expensive.
- - Dashlane: includes VPN and remote access revocation; above-average pricing.
What to consider when choosing a password manager
- - Password generator
- - Password strength reports
- - Two-factor authentication
- - Application-level password management
- - Automatic password change features
- - Multi-device synchronization
Some managers integrate with authenticator apps, adding an extra layer of security.
Reminder: never share your master password, it is the key to your digital vault.
Passwords remain one of the biggest weaknesses in cybersecurity, but the good news is that with simple practices - strong passwords, multi-factor authentication (MFA) and password managers - risks can be significantly reduced.
Wilde Artikel
Artificial Intelligence in Cybersecurity: How it is transforming attacks and digital defence
How a functional analyst transforms requirements into solutions
Learning to Program in .NET – What You Need to Get Started
The role of COBOL in banking infrastructure
RPG/AS400: How this technology keeps up with digital advancements
Essential skills for functional analysts
